
New HITRUST assessments rise to meet the need for varying assurance levels
Exploring the expanded HITRUST assessment portfolio: bC, i1 and r2
With the wide variety of assurance service offerings in the marketplace today, organizations are struggling to discern how much assurance they need as well as what types of compliance efforts they should be providing to their clients. On top of that, there’s confusion over how the various HITRUST levels fit in with the assessments they are already performing.
During a recent webinar, Michael Parisi, vice president of adoption at HITRUST, and Samantha Boterman, senior manager in Baker Tilly risk advisory, discussed the differences among HITRUST’s three assessment types and how they work at all maturity compliance levels.
Boterman said the challenges and questions organizations are having typically revolve around a couple of issues, including finding a way to provide credible and reliable information risk management assurances not only to relying parties but also to fulfill internal information protection assurance requirements. Another leading concern is the potential waste of time and resources performing duplicative assessments to satisfy multiple compliance frameworks (as opposed to “test once and apply/report to many”).
Still, the primary question is: What type of information protection assessment is right for my organization?
Not all assurance mechanisms are created equal, Parisi said. Organizations have a number of different attributes to consider whether they are pursuing an assurance mechanism to provide comfort to their stakeholders or just considering the type they are willing to accept in place of, perhaps, executing additional proprietary procedures around security and privacy. When organizations are trying to understand what assurance reports or certifications to use, it’s not clear to stakeholders the differences among them.
To clarify the options, HITRUST conducted a 16-month research project in which it plotted all of the assurance mechanisms along a continuum and identified the different attributes and characteristics that made them provide varying levels of assurance. From there, HITRUST found two primary drivers.
- The first was that many of the assurance mechanisms were based on management-defined proprietary controls, which means they may not be from an industry-recognized source or may not align to specific compliance factors or security standards, Parisi said. This could lead to a high level of inconsistency when trying to evaluate across multiple business stakeholders.
- The second identified driver was the rigor of the process that organizations go through in order to produce assurances. At one extreme is self-attestation where there is no level of independent validation, which provides a much lower level of comfort relative to the program maturity and posture as opposed to if it was performed using independent validation and, moreover, if there was a certifying body, like HITRUST, that provided additional validation.
What this data told HITRUST was that the moderate assurance realm of the continuum was lacking so smaller organizations didn’t have the assurance mechanism options they needed. The lower realm was also missing a level of quality assurance as all that were available were self-attestations. Further, there was no assurance mechanism to help organizations address the most common cyber threats and risks.
Based on its findings, HITRUST added two levels to its portfolio: Basic Current State (bC) Self-Assessment and Implemented One-Year (i1) Validated Assessment. It also renamed its existing HITRUST CSF Validated Assessment to Risk-based, Two-Year (r2) Validated Assessment.
The two new assessment types, bC and i1,offer a level of transparency, consistency, accuracy and integrity that isn’t typically seen at the low or moderate level of assurance. Boterman explained that even though these new service offerings are at a low or moderate level of rigor of controls, HITRUST has provided transparency into the understanding of what the controls are, how they were selected and what’s being adopted for scoring. As far as consistency, many of the lower level frameworks can be subjective with no kind of maturity levels or scoring methodology. HITRUST has a formalized scoring and evaluation model to address the control environment. When it comes to accuracy, HITRUST provides clear insight for when an organization is using sub-service organizations, and how their controls and the sharing of those control responsibilities can get brought into the HITRUST assessment. Finally, the integrity of the assessment reports and assurances is evident since they can show the methodology, the testing, the deliverables and the levels of review to both internal and external stakeholders. And, unlike other frameworks, they are being reviewed not only by an external organization and assessor entity but also a standards body, HITRUST.
Furthermore, because HITRUST is so adaptive, the size of the organization or how new it is to compliance doesn’t necessarily dictate the best assessment to start with. Some smaller organizations may have rock-solid compliance and will feel comfortable going for an r2 assessment the first time around. Internal discussions around client expectations for what level of assurance they want will help determine the assessment level the organization should pursue.
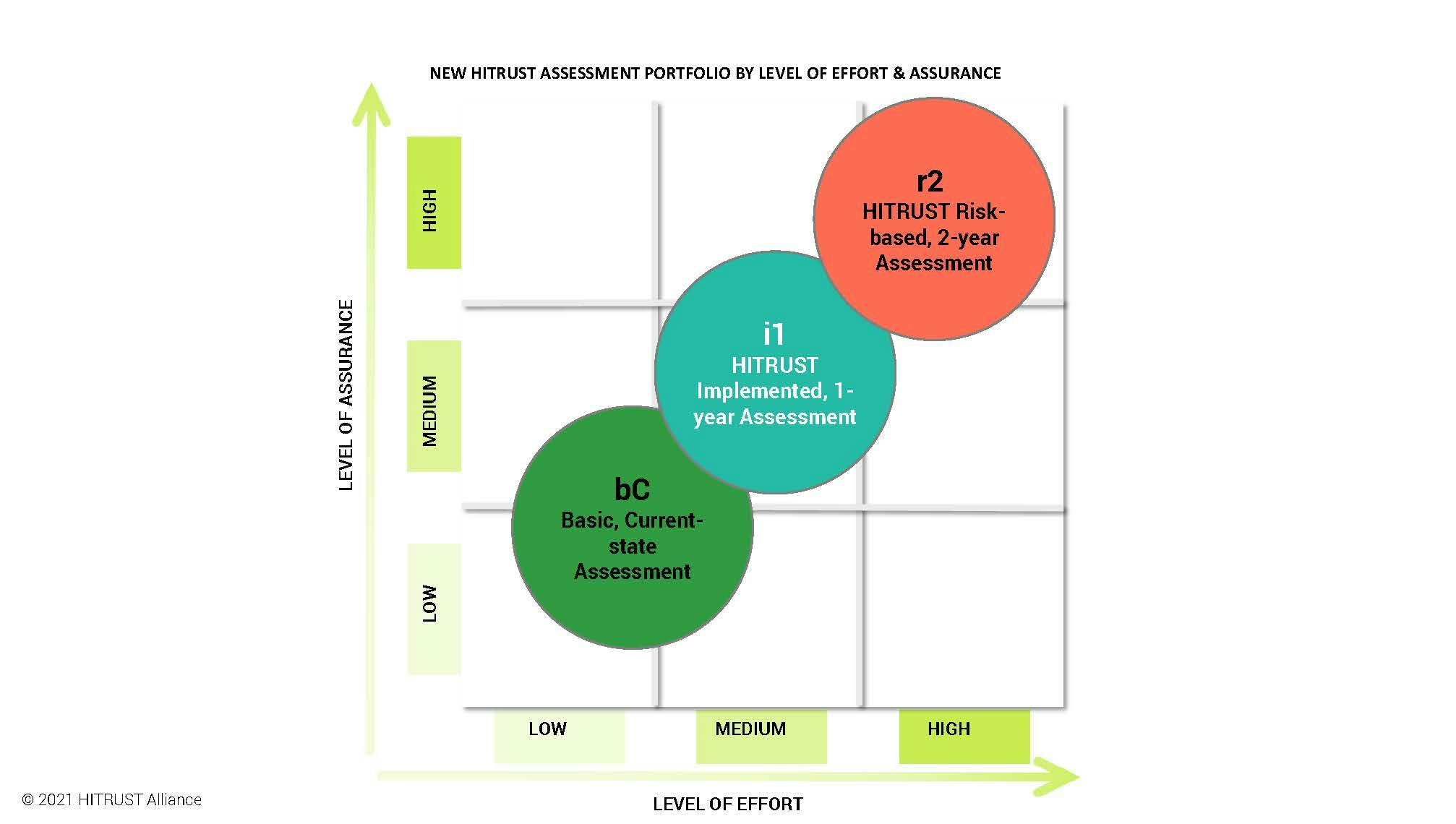
Starting with HITRUST bC, this assessment involves the lowest levels of effort and assurance, focusing on “good security hygiene controls.” The best candidates for this level are new market entrants, startups or organization that have never undergone compliance efforts before. This gives them the opportunity to ease into the HITRUST process and methodology, which tends to be a little different as it does have a quality assurance element and a governing body executing the final report. It will also help an organization start its road map toward an i1 or r2 assessment.
The i1 assessment is next on the continuum. This level is for organizations that have undergone some other compliance regulations already, and because of growth in certain areas may now be required to attain a higher level of assurance. This really focuses on an operation’s effectiveness. It’s not as comprehensive or intense as the HITRUST r2, but it is for use when the organization is following leading security practices and getting familiar with the more formal audit assessor area. It has the benefit of the third-party assessor and the HITRUST organization for the second level of assurance. In addition, the i1 is threat-adaptive, which means that as the threat landscape evolves, the HITRUST CSF framework and i1 requirements will be updated to remain cyber-relevant over time to reduce future risk.
The r2 is the most rigorous assessment, with a certification covering two years. It is a more comprehensive risk-based approach that gets to a granular level of detail over the environment as a whole, beyond just best practices. It provides the highest level of assurance so that when the organization has completed the r2, the results can be used again for other assurance reporting, achieving the goal of “test once and report to many” that was mentioned earlier. Organizations at this level have hit the pinnacle of good security hygiene and are properly applying the regulations placed on them. By design, it is not easy to achieve.
With all of that said, not every organization needs to reach r2. They may never need to provide assurances above and beyond a bC or an i1. They just need an industry-recognized assessment mechanism appropriate for their level of risk.
