
Navigating the NAIC Insurance Data Security Model Law
In response to an increasing number of data breaches impacting the insurance industry, the National Association of Insurance Commissioners (NAIC) formulated the Insurance Data Security Model Law[1] which was ratified during the NAIC Summer 2017 National Meeting. With the development of this national guidance, a uniform set of data security requirements, including a risk based information security program, has been established to help aid in the protection of personally identifiable consumer data. As more states adopt the model into applicable state law, insurers throughout the U.S. will need to continue to strengthen their cybersecurity programs.
Exemptions
An important detail to note is that the law exempts licensees with fewer than 10 employees, licensees compliant with the Health Insurance Portability and Accountability Act of 1996 (HIPAA), and agents of a licensee from Section 4 of the model. The model also does not create a private cause of action, nor does it limit an already existing private right of action.
Key considerations
To help insurers understand the regulation and develop their compliance assessment, the following is a list of the model law’s provisions and key areas to consider when reviewing your information security management program:
Section 3. Definitions
When managing an information security program, the critical starting point is to align to a common set of defined terminology. When companies are looking to implement compliance programs, starting with an understanding of the key terminology and definitions is a good place to start. For well-developed information security programs, starting over with defining terms may be wasteful. Instead, organizations should look to map or align their definitions to that of the law. A document that includes a glossary of the company’s cybersecurity policies and procedures that are aligned with the law will help demonstrate compliance.
Section 4. Information Security Program
4(A) Implementation of an Information Security Program and 4(B) Objectives of Information Security Program
A risk based information security program should be designed and implemented to:
- Protect the security and confidentiality of nonpublic information and the security of the information system.
- Protect against any threats or hazards to the security or integrity of nonpublic information and the information system.
- Protect against unauthorized access to or use of nonpublic information, and minimize the likelihood of harm to any consumer.
- Define and periodically reevaluate a schedule for retention of nonpublic information and a mechanism for its destruction when no longer needed.
4(C) Risk Assessment
Many sections of the law are risk-based, which is why conducting risk assessment exercises should be a significant undertaking. As businesses and the risks they are exposed to continue to evolve, it is imperative that companies maintain a feedback loop in their assessment process to ensure risks are being assessed with current information and resources are adequately deployed to the highest risk areas.
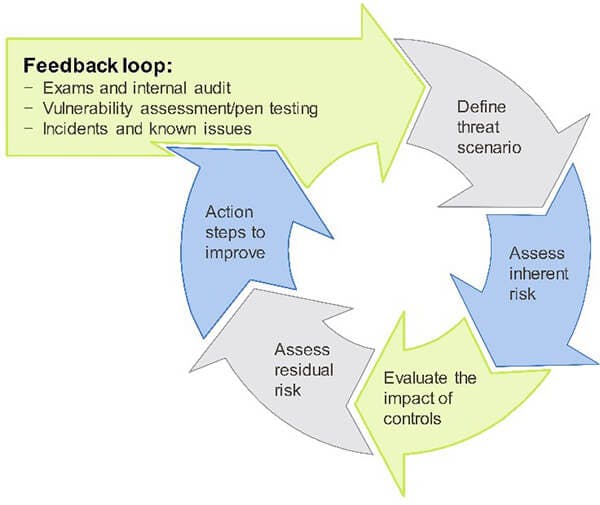
An important item to consider is the planned action steps stemming from the risk assessment. Considering the elements identified as planned improvements from the risk assessment process, it is important that companies illustrate how each of the identified items from the last assessment were addressed and how milestones for planned improvements will be monitored.
The risk assessment process should be tailored to your organization, but minimally include the following:
- Formally designate a person(s) or entity to be responsible for the execution of the risk assessment, as well as the implementation and operation of the information security program.
- Develop and implement risk assessment policies and procedures that address:
- How and when risk assessments are performed
- How risk is categorized and treated (e.g., accepted, avoided, mitigated, etc.)
- How risk treatment is reported and managed (e.g., likelihood, impact, etc.)
- Investigate the systems and internal locations for the storage and movement of nonpublic information.
- Conduct a thorough risk assessment of information systems that process, store and communicate nonpublic information in accordance with risk assessment policy.
- Assess and treat identified risks in accordance with risk management policy.
- Assess the sufficiency of existing policies, procedures, information systems and other safeguards.
- Establish a system for tracking identified vulnerabilities and their risk treatment.
- Conduct annual control operational effectiveness testing and summarize the results.
4(D) Risk Management
For the purpose of managing risk, the law requires the information security program to address concerns associated with the protection of information systems that process, store or communicate nonpublic information, including:
- Control of user logical access to information systems.
- Maintenance of a complete and accurate IT asset inventory.
- Control of user physical access to information systems.
- Use of data encryption or approved compensating controls to mitigate data-at-rest risks and use of transmission encryption or approved compensating controls to mitigate data-in-motion risks.
- Establishment of security policy, standards and procedures for the development and procurement of secure applications.
- Control of changes made to all information systems that process, store or communicate nonpublic information.
- Implementation of multi-factor authentication for access to information systems.
- Regular assessment monitoring of all information systems for vulnerabilities and weaknesses, and continuous security event monitoring, annual penetration testing, and vulnerability scanning.
- Establishment of security event and financial transaction logging capabilities to create audit trails.
- Establishment of a backup strategy to protect information systems from loss due to technical and environmental issues.
- Creation and implementation of a data governance and classification policy.
The law also requires the establishment of a process to ensure the company is keeping up-to-date with emerging cybersecurity threats and countermeasures. Keeping current with emerging risks and threats may seem like an insurmountable task, but the key to doing this well is by establishing a process for in-taking information, analyzing its impact and responding accordingly. Participating in the Financial Services Information Sharing and Analysis Center (FS-ISAC) and InfraGard are excellent sources of information and knowledge sharing. There are also countless resources from various government agencies, security service providers and industry websites and blogs. Companies need to define which information sources they will be using and remain diligent in applying their process of intake, analysis and response.
Surprisingly, despite cybersecurity being in the news and all the effort put toward educating personnel, people remain the biggest risk to maintaining a secure environment. Regular training of information security staff, executives, directors and personnel remains paramount to maintaining an effective cybersecurity program. Helping to round out a robust risk management program, the law requires security awareness training to be administered on relevant and current content. An effective training program also includes a mechanism through which completion is evidenced, and employee performance is assessed and evaluated. Ideally, employees illustrating deficiencies through evaluations should receive enhanced training to increase their cybersecurity awareness. An effective way to assess employee behavior is to consider combining social engineering exercises with security awareness training by creating a feedback loop that highlights and reinforces good behavior.
4(E) Oversight by Board of Directors
Boards need to establish the requirement for executive management or a delegate to develop, implement and maintain an information security program. Executive management must oversee any delegation of its responsibilities and ensure delegate compliance with the law. On at least an annual basis, executive management, or the delegate, is required to report to the board information about:
- The overall status of the information security program and compliance with the law
- Material matters related to the information security program, addressing issues such as risk assessment, risk management, control decisions and third party service provider arrangements
- Testing results
- Cybersecurity events or violations and management’s responses
- Recommendations for changes in the information security program
4(F) Oversight of Third-Party Service Provider Arrangements
One of the largest undertakings in the compliance journey with this regulation is the improvement of a third party management program. A third party service provider policy should be established outlining the process for evaluating and monitoring third party vendors, as well as the minimum cybersecurity standards to be met by providers. To ensure a company meets the requirements of the regulation, organizations should:
- Maintain an inventory of third party service providers
- Define the risk factors to be used in evaluating third-parties:
- Type of data stored, transferred and processed (i.e., PII, PHI, PCI, etc.)
- Type of service
- Criticality to operations
- Financial impact (i.e., how much they are paid)
- Known issues, including breaches
- Assess the third party service providers using the defined criteria
- Perform a review cycle based on the risk ratings
- Ensure the process is followed for each new vendor
Due to the potential volume of vendors and difficulty to obtain the needed information to properly risk rank the vendors, the model law suggests a two (2) year lag for required effective date from date of adoption (compared to the standard one (1) year for the rest of the regulation).
4(G) Program Adjustments
The model law requires your information security program to evolve as the organization does. It requires organizations to assess, reassess and make adjustments based on changes in technology, the sensitivity of its nonpublic information, internal or external threats to information and changing of business arrangements (e.g., mergers and acquisitions, alliances and joint ventures, outsourcing arrangements, changes to information systems, etc.). In many circumstances, a formal risk assessment should be conducted to determine any necessary adjustments. Documentation supporting the completed assessment and adjustments to the information security program should be retained for future reference.
4(H) Incident Response Plan
The model law calls for the creation of an incident response plan. It’s fairly standard to assume your organization will experience some level of data loss or breach, therefore the model law looks to enforce a well-developed response plan is in place. An effective incident response plan should address:
- The internal process for responding to a cybersecurity event
- The goals of the incident response plan
- The definition of clear roles, responsibilities and levels of decision-making authority
- External and internal communication protocols
- Assessment of impact to constituents
- Documentation and reporting regarding cybersecurity events and related incident response activities
- Conducting a post mortem on events and revision of the incident response plan following a cybersecurity event
It is also crucial to test the incident response plan. At a minimum, companies should conduct a table top exercise involving all relevant incident response team members and stakeholders. During the exercise, several mock incidents are introduced and the team is given a defined length of time to formulate a response. After the team discusses and modifies their responses, the incident response plan is reviewed to determine any necessary modifications or to add any addendums regarding planned responses to specific events.
4(I) Annual Certification to Commissioner of Domiciliary State
For the purpose of evidencing and certifying compliance with Section 4 of the law, companies are required to:
- Submit an annual written statement, certifying compliance by Feb. 15 of the subsequent year
- Retain schedules and data supporting annual certifications for a period of five years
- Retain documentation supporting material system improvements
Thus far, most of the states which have adopted the regulation have adopted the suggested implementation timeframes as well, which are one (1) year from the date of adoption to comply with all sections of the regulation with the exception being for Section 4F related to third party service provider oversight. These effective dates trigger the need for compliance certification on Feb. 15 of the year following “effective.”
Section 5. Investigation of a Cybersecurity Event
Along the similar notion that most companies will experience some type of data loss or breach, the model law includes requirements around the investigation and notification of a cybersecurity event. A well-defined process for investigating cybersecurity events is crucial for mitigating damages associated with the unauthorized disclosure of nonpublic information due to a breach. The incident response plan (discussed in Section 4H) should define the roles and responsibilities, and outline the investigative procedures that need to be implemented. Investigative procedures must also be executed for both in-house systems and systems maintained by third party service providers. The records supporting the completed investigations need to be retained for at least five (5) years and must:
- Determine whether an actual cybersecurity event has occurred
- Assess the nature and scope of the cybersecurity event
- Identify nonpublic information that may have been involved in the cybersecurity event
- Take reasonable measures to restore the security of compromised systems and prevent reoccurrence
Section 6. Notification of a Cybersecurity Event
As any oversight body would advise, the model law requires a notification to be made to the governing body when a cybersecurity event was deemed to have occurred. To assist in making this process as seamless as possible, it is important to establish formal processes for determining whether a cybersecurity event requires notification to the commissioner, consumers, reinsurers to insurers and/or insurers to producers of record. Notification procedures must be applied to the unauthorized disclosure of nonpublic information contained both with in-house and third party service provider operated systems. Company management should also study the law and establish documented process flows for deciding who to notify and how to communicate that an incident has occurred. The process flows should identify key systems and data types contained within key stakeholders, technical staff and members of the internal/external legal teams who will be involved in the process. In general, the law requires notification to occur within 72 hours from a determination that a cybersecurity event has occurred and involves 250 or more consumers; however, as each state adopts the model law, these values are likely to differ from state to state.
Section 7. Power of Commissioner
With the adoption of the model law, the insurance commissioner is granted the power to examine insurance entities for compliance with their adopted data security regulation. Many states are performing these exams currently if their respective legislature has enacted the law. In order to comply with examinations initiated by the commissioner, companies should ensure that adequate evidence is retained to support compliance with each section of the law. The evidence should be stored so that it is accessible when needed and documented so a reasonable person can draw a similar conclusion. Ideally, companies will utilize internal audit to conduct a review of the documentation to provide feedback regarding the status of supporting documentation; this will help expedite the exam process and likely reduce the risk of areas being overlooked.
Wrapping up the NAIC Insurance Data Security Model Law
Now that states are in the process of adopting, or have already adopted the NAIC Insurance Data Security Model Law, it is vital for insurance organizations to take a fresh look at their cybersecurity management program, determine areas for enhanced security or compliance, and be prepared for your state’s next cybersecurity examination.
For more information on this topic, or to learn how Baker Tilly cybersecurity specialists can assist you, contact our team.
[1] Insurance Data Model Security Law (2017), retrieved from https://content.naic.org/sites/default/files/inline-files/MDL-668.pdf.
© 2024 Baker Tilly US, LLP
