Article
How higher education and research institutions may benefit from using HITRUST to navigate research data security requirements
Research dollars and data now come with more terms and conditions than ever before. Many of these “newer” requirements are related to previous efforts to protect the current and future value of information or data, especially when funded by the federal government. Unfortunately, grants, contracts and cooperative agreements contain so many disparate research security requirements and terms that it can be difficult to determine what is most important for your institution to address.
To effectively address these requirements, stakeholders from across the institution must work together, as this is not simply an administrative, technology or cybersecurity problem. The latest developments regarding research security requirements, including National Security Presidential Memo 33 (NSPM-33), Controlled Unclassified Information (CUI), Export Controls, and Cybersecurity Maturity Model Certification (CMMC), all involve implementing a variety of people, process and technology controls.
As such, higher education and research institutions are looking for new and effective ways to navigate these research security requirements within their complex, distributed and diverse environments.
How can HITRUST help higher education and research institutions address regulated research data security requirements, such as NIST, that are different from HITRUST controls?
The HITRUST CSF provides coverage across multiple industry-specific standards and includes significant components from other well-respected information technology (IT) security standards bodies and governance sources, such as the National Institute of Standards and Technology (NIST) and International Organization for Standardization (ISO) 27001. HITRUST contains a minimum set of control requirements that organizations must implement. Institutions then obtain the complete, tailored set of control requirements (controls) necessary for certification based on certain categories of risk factors such as organizational, system, geographical and regulatory risks. This allows an institution to address different research data security requirements within one framework.
How can a HITRUST assessment help my institution if we do not need to be HITRUST certified?
HITRUST offers multiple assessment types that can be utilized to satisfy contractual requirements, internal control environment requirements and due diligence with regulatory authorities and other external stakeholders.
HITRUST is widely adopted in the healthcare industry, but with HITRUST’s continued expansion of authoritative sources included within the CSF and the release of new threat-adaptive assessment options, the door has opened to other industries. Now, higher education and research institutions that traditionally may not have considered HITRUST as an optional framework are making a shift to leverage HITRUST as threats to securing sensitive data (e.g., electronic protected health information (ePHI), intellectual data) continue to rise.
Which assessment type is right for my regulated research organization?
Assessment types are not ‘one size fits all,’ but HITRUST has expanded its assessment portfolio to address the varying needs of different institutions:
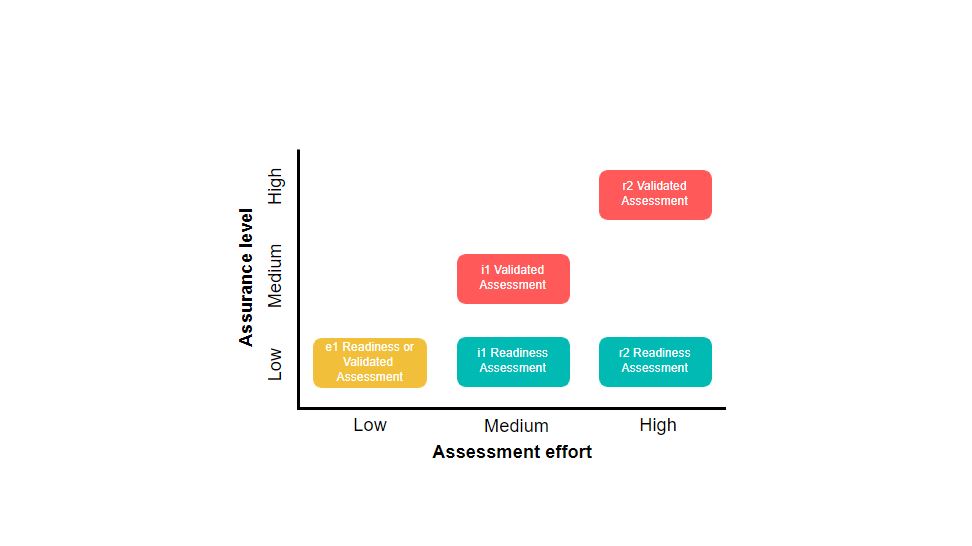
- HITRUST Essentials, 1-year Validated Assessment
A readiness or validated assessment certifiable by HITRUST focusing on essential, foundational cybersecurity hygiene, which provides a low level of assurance. Most closely considered a readiness or verified self-assessment, which provides a low level of assurance. There are 44 control requirements in scope. The e1 Assessment is a replacement for the bC in Version 11 and later of the HITRUST CSF framework. - HITRUST Implemented, 1-year (i1) Validated Assessment
Certifiable by HITRUST and is considered a moderate level of assurance. The organization and the external assessor (e.g., Baker Tilly) will utilize the MyCSF Tool to manage and score 182 control requirements. This is an annual assessment that provides coverage over the fixed control requirements over the implementation of the controls only. If your organization does not have ePHI, this is a recommended assessment option (considering no other major factors). For the interim period, an i1 Rapid Recertification allows for a more streamlined approach to earn an additional certification year by only assessing a subset of i1 requirements. - HITRUST Risk-Based, 2-year (r2) Validated Assessment
This assessment is considered a comprehensive risk-based assessment for a rigorous approach to security and privacy. This is a tailored approach and control requirements can range up to 2,000+ (average is 360). The maturity assessment of the control requirements includes an external assessor evaluation of at least policy, procedure, and implementation. The validated assessment is certifiable and involves the HITRUST quality assurance (QA) process every two years.
The diagram below highlights the available assessment options and maps the level of assurance conveyed against the level of effort required to achieve it.
Are other higher education and research institutions using HITRUST?
Certain higher education and research institutions are taking steps to move towards the HITRUST framework. Earlier in 2022, the Regulated Research Community of Practice (RRCoP) began building a professional network to aid with developing an affordable yet effective cybersecurity and compliance program for use by higher education and research institutions. Some of these organizations have chosen HITRUST as their guiding program to help provide reliable assurances to their stakeholders and we expect more to follow.
Through this project, RRCoP helps:
- Develop cybersecurity training resources that share validated and diverse best practices.
- Establish a leadership training and development program accelerating the availability of distributed university resources.
- Build representation through strategic partnerships with industry and government entities. By supporting the community with the development of a strategic road map, regular discussions and workshops, and a repository of generalized and specific resources for handling regulated research programs.
One of the collaborating partners for the RRCoP is HITRUST for data security and government regulations. The RRCoP has opted to partner with HITRUST as their updated assessment options have opened a door for these institutions to follow a rigorous yet manageable framework. “HITRUST’s ‘assess once, report many’ approach aligns well to the RRCoP’s mission to help academic organizations navigate a complex regulatory landscape,” said Michael Parisi, vice president of adoption at HITRUST. “The HITRUST approach is about managing risk as efficiently and effectively as possible, which enables these entities to do a single assessment to meet the assurance requirements of various stakeholders.”
For more information on this topic, or to learn how Baker Tilly Value Architects™ can help your higher education and research institution explore HITRUST, contact our team.
Learn more.

Higher Education
Higher education transformation is a journey. Let's embark on it, together.
HITRUST CSF Assessment Services
The HITRUST CSF provides an integrated, certifiable approach to securing PHI. Any organization handling PHI on behalf of customers may be required to obtain a HITRUST CSF certification.
Cybersecurity
Proactively protect and address your cybersecurity and information technology (IT) risks.
Footnote: Baker Tilly has been a HITRUST Assessor Firm since 2016 and sits on the External Assessor Council.